IP Route Management
Document revision 1.4 (01-Jun-2003)This document applies to the MikroTik RouterOS V2.7
Table of Contents
- Table of Contents
- Summary
- Specifications
- Related Documents
- Description
- Static Routes
- Policy Routing
- Application Example
- Additional Resources
Summary
The following Manual discusses managing the IP routes, equal-cost multi-path (ECMP) routing technique as well as policy-based routing, which give opportunity to select routes in order to restrict the use of network resources to certain classes of customers.Specifications
Packages required : systemLicense required : Any
Home menu level : /ip route, /ip policy-routing
Protocols utilized : IP (RFC791)
Hardware usage: not significant
Related Documents
Software Package Installation and UpgradingIP Addresses and Address Resolution Protocol (ARP)
Packet Filter (Firewall) and Network Address Translation (NAT)
Description
MikroTik RouterOS has following types of routes:- Connected Routes are created automatically when adding address to an interface. These routes specify networks, which can be accessed directly through the interface.
- Static Routes are user-defined routes that specify the router that can forward traffic to the specified network. They are useful for specifying the default gateway.
You do not need to add routes to networks directly connected to the router, since they are added automatically when adding the IP addresses. However, unless you use some routing protocol (RIP or OSPF), you may want to specify static routes to specific networks, or the default route.
More than one gateway for one destination network may be used. This approach ir called 'Equal Cost Multipath Routing' and is used for load balancing (Note that this does not provide failover). With equal cost multipath, a router potentially has several available next hops towards any given destination. A new gateway is chosen for each new source/destination IP pair. This means that, for example, one FTP connection will use only one link, but new connection to a different server will use other link. This also means that routes to often-used sites will always be over the same provider. But on big backbones this should distribute traffic fine. Also this has another good feature - single connection packets do not get reordered and therefore do not kill TCP performance.
Equal cost multipath routes can be created by routing protocols (RIP or OSPF), or adding a static route with multiple gateways (in the form gateway=x.x.x.x,y.y.y.y) The routing protocols may create routes with equal cost automatically, if the cost of the interfaces is adjusted properly. For more information on using the routing protocols, please read the corresponding section of the Manual.
Static Routes
Submenu level : /ip routeProperty Description
dst-address (IP address/mask) - destination address and network mask, where netmask is number of bits which indicate natwork numbernetmask (IP address) - network mask
gateway (IP address) - gateway host, that can be reached directly through some of the interfaces. You can specify multiple gateways separated by comma "," for equal cost multipath routes. See more information on that below
preferred-source (IP address; default: 0.0.0.0) - source address of packets leaving the router via this route. Must be a valid address of the router, which is assigned to the router's interface, through which the packet leaves
distance (integer; default: 1) - administrative distance of the route. When forwarding a packet the router will use the route with the lowest administrative distance and reachable gateway.
Statistics:
gateway-state (r | u) - shows the status of the next hop. Can be r (reachable) or u (unreachable)
interface (name) - interface through which the gateway can be reached
Notes
You can specify more than one or two gateways in the route. Moreover, you can repeat some routers in the list several times to do a kind of cost setting for gateways.
Example
To add two static routes to networks 192.168.0.0/16 and 0.0.0.0/0 (the default destination address) on a router with two interfaces and two IP addresses:
[admin@MikroTik] ip route> add dst-address=192.168.0.0/16 gateway=10.10.10.2
[admin@MikroTik] ip route> add gateway 10.10.10.1
[admin@MikroTik] ip route> print
Flags: X - disabled, I - invalid, D - dynamic, J - rejected,
C - connect, S - static, r - rip, o - ospf, b - bgp
# DST-ADDRESS G GATEWAY DISTANCE INTERFACE
0 S 192.168.0.0/16 r 10.10.10.2 1 Local
1 S 0.0.0.0/0 r 10.10.10.1 1 Public
2 DC 10.10.10.0/24 r 0.0.0.0 0 Public
[admin@MikroTik] ip route> print detail
Flags: X - disabled, I - invalid, D - dynamic, J - rejected,
C - connect, S - static, r - rip, o - ospf, b - bgp
0 S dst-address=192.168.0.0/16 preferred-source=0.0.0.0
gateway=10.10.10.2 gateway-state=reachable distance=1
interface=Local
1 S dst-address=0.0.0.0/0 preferred-source=0.0.0.0 gateway=10.10.10.1
gateway-state=reachable distance=1 interface=Public
2 DC dst-address=10.10.10.0/24 preferred-source=10.10.10.1
gateway=0.0.0.0 gateway-state=reachable distance=0 interface=Public
To set the 192.168.0.0/16 network is reachable via both 10.10.10.2
and 10.10.10.254 gateways:
[admin@MikroTik] ip route> set 0 gateway=10.10.10.2,10.10.10.254
[admin@MikroTik] ip route> print
Flags: X - disabled, I - invalid, D - dynamic, J - rejected,
C - connect, S - static, r - rip, o - ospf, b - bgp
# DST-ADDRESS G GATEWAY DISTANCE INTERFACE
0 S 192.168.0.0/16 r 10.10.10.2 1 Local
r 10.10.10.254 Local
1 S 0.0.0.0/0 r 10.10.10.1 1 Public
2 DC 10.10.10.0/24 r 0.0.0.0 0 Public
[admin@MikroTik] ip route>
Policy Routing
Description
Policy routing allows select routes in order to variate the use of network resources to certain classes of users (in other words, you can set different routes to the same networks depending on some classifiers). This is implemented using multiple routing tables and a list of rules specifying how these tables should be used.The Policy Routing is implemented in the MikroTik RouterOS based on source and destination addresses of a packet, the interface the packet arrives to the router and the firewall mark that may be associated with some packets.
When finding the route for a packet, the packet is matched against policy routing rules one after another, until some rule matches the packet. Then action specified in that rule is executed. If no rule matches the packet, it is assumed that there is no route to given host and appropriate action is taken (packet dropped and ICMP error sent back to the source).
If a routing table does not have a route for the packet, next rule after the one that directed to the current table is examined, until the route is found, end of rule list is reached or some rule with action drop or unreachable is hit. Thus it is good to have last rule say "from everywhere to everywhere, all interfaces, lookup main route table", because then gateways can be found (connected routes are entered in the main table only).
Note that the only way for packet to be forwarded is to have some rule direct to some routing table that contains route to packet destination.
Routing Tables
Submenu level : /ip policy-routingDescription
Routing tables is a way to organize routing rules into groups for a purpose of easy management. These tables can be created/deleted in the /ip policy-routing menu.The routes in the routing tables are managed the same way as the static routes described above, but in the submenu /ip policy-routing table name submenu, where name is name of the table
Property Description
name (name) - table nameNotes
There is always the table main - this one can not be deleted and its name can not be changed. The main table can be managed in in the /ip route submenu as well:
[admin@MikroTik] ip policy-routing> table main
[admin@MikroTik] ip policy-routing table main> print
Flags: X - disabled, I - invalid, D - dynamic, R - rejected
# TYPE DST-ADDRESS G GATEWAY DISTANCE INTERFACE
0 static 192.168.1.0/24 r 192.168.0.50 1 Local
1 static 0.0.0.0/0 r 10.0.0.1 1 Public
2 D connect 192.168.0.0/24 r 0.0.0.0 0 Local
3 D connect 10.0.0.0/24 r 0.0.0.0 0 Public
[admin@MikroTik] ip policy-routing table main>
[admin@MikroTik] ip policy-routing table main> /ip route print
Flags: X - disabled, I - invalid, D - dynamic, J - rejected,
C - connect, S - static, R - rip, O - ospf, B - bgp
# DST-ADDRESS G GATEWAY DISTANCE INTERFACE
0 S 192.168.1.0/24 r 192.168.0.50 1 Local
1 S 0.0.0.0/0 r 10.0.0.1 1 Public
2 DC 192.168.0.0/24 r 0.0.0.0 0 Local
3 DC 10.0.0.0/24 r 0.0.0.0 0 Public
[admin@MikroTik] ip policy-routing table main>
Example
To add a new table named mt:[admin@MikroTik] ip policy-routing> add name=mt [admin@MikroTik] ip policy-routing> print Flags: D - dynamic # NAME 0 mt 1 D main [admin@MikroTik] ip policy-routing>To add the route to the 10.5.5.0/24 via 10.0.0.22 gateway to the mt table:
[admin@MikroTik] ip policy-routing> table mt [admin@MikroTik] ip policy-routing table mt> add dst-address=10.5.5.0/24 \ \... gateway=10.0.0.22 [admin@MikroTik] ip policy-routing table mt> print Flags: X - disabled, I - invalid, D - dynamic, R - rejected # TYPE DST-ADDRESS G GATEWAY DISTANCE INTERFACE 0 static 10.5.5.0/24 r 10.0.0.22 1 Public [MikroTik] ip policy-routing table mt>
Policy rules
Submenu level : /ip policy-routing ruleProperty Description
src-address (IP adress/mask) - source IP address/maskdst-address (IP adress/mask) - destination IP address/mask
interface (name | all; default: all) - interface name through which the packet arrives. Should be all for the rule that should match locally generated or masqueraded packets, since at the moment of processing the routing table these packets have interface name set to loopback
flow (name; default: "") - flow mask of the packet to be matched by this rule
action (drop | unreachable | lookup; default: unreachable) - action to be processed on packets to be matched by this rule:
Notes
Policy routing will not function 'as desired' for packets originated from the router or masqueraded packets. It is because these packets have source address 0.0.0.0 at the moment when they are processed by the routing table. Therefore it is not possible to match masqueraded packets by source address with policy routing rule. You should use matching by flow together with packet marking instead.Example
To add the rule specifying that all the packets from the 10.0.0.144 host should lookup the mt routing table:[admin@MikroTik] ip policy-routing rule> add src-address=10.0.0.144/32 \ \... table=mt action=lookup [admin@MikroTik] ip policy-routing rule> print Flags: X - disabled, I - invalid # SRC-ADDRESS DST-ADDRESS INTE... FLOW ACTION TABLE 0 0.0.0.0/0 0.0.0.0/0 all lookup main 1 10.0.0.144/32 0.0.0.0/0 all lookup mt [admin@MikroTik] ip policy-routing rule>
Application Example
Suppose we want packets coming from 1.1.1.0/24 to use gateway 10.0.0.1 and packets from 2.2.2.0/24 to use gateway 10.0.0.2. And the rest of packets will use gateway 10.0.0.254 (assuming we already have it):
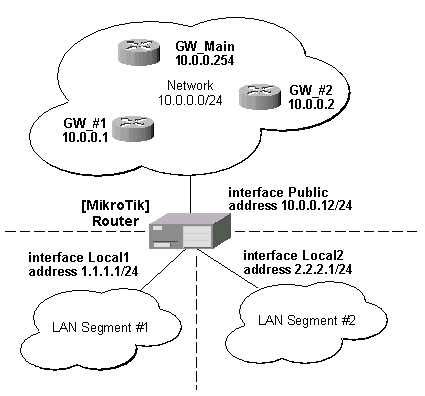
Command sequence to achieve this:
- Add 2 new routing tables:
[admin@MikroTik] ip policy-routing> add name=from_net1; add name=from_net2 [admin@MikroTik] ip policy-routing> print Flags: D - dynamic # NAME 0 from_net1 1 from_net2 2 D main [admin@MikroTik] ip policy-routing>
- Create the default route in each of the tables:
[admin@MikroTik] ip policy-routing> table from_net1 add gateway=10.0.0.1 [admin@MikroTik] ip policy-routing> table from_net2 add gateway=10.0.0.2 [admin@MikroTik] ip policy-routing> table from_net1 print Flags: X - disabled, I - invalid, D - dynamic, R - rejected # TYPE DST-ADDRESS G GATEWAY DISTANCE INTERFACE 0 static 0.0.0.0/0 u 10.0.0.1 1 Public [admin@MikroTik] ip policy-routing> table from_net2 print Flags: X - disabled, I - invalid, D - dynamic, R - rejected # TYPE DST-ADDRESS G GATEWAY DISTANCE INTERFACE 0 static 0.0.0.0/0 u 10.0.0.2 1 Public [admin@MikroTik] ip policy-routing>
- Create rules that will direct traffic from sources to given tables,
and arrange them in the desired order:
[admin@MikroTik] ip policy-routing> rule [admin@MikroTik] ip policy-routing rule> print Flags: X - disabled, I - invalid # SRC-ADDRESS DST-ADDRESS INT... FLOW ACTION 0 0.0.0.0/0 0.0.0.0/0 all lookup [admin@MikroTik] ip policy-routing rule> add src-address=1.1.1.1/32 \ \... action=lookup table=main [admin@MikroTik] ip policy-routing rule> add src-address=2.2.2.1/32 \ \... action=lookup table=main [admin@MikroTik] ip policy-routing rule> add src-address=1.1.1.0/24 \ \... action=lookup table=from_net1 [admin@MikroTik] ip policy-routing rule> add src-address=2.2.2.0/24 \ \... action=lookup table=from_net2 [admin@MikroTik] ip policy-routing rule> print Flags: X - disabled, I - invalid # SRC-ADDRESS DST-ADDRESS INT... FLOW ACTION 0 1.1.1.1/32 0.0.0.0/0 all lookup 1 2.2.2.1/32 0.0.0.0/0 all lookup 2 1.1.1.0/24 0.0.0.0/0 all lookup 3 2.2.2.0/24 0.0.0.0/0 all lookup 4 0.0.0.0/0 0.0.0.0/0 all lookup [admin@MikroTik] ip policy-routing rule>
Additional Resources
Recommended readings for guidelines on routing issues:
© Copyright 1999-2003, MikroTik