MikroTik RouterOS V2.4 Firewall Filters
Document revision 11-Oct-2001
This document applies to the MikroTik RouterOS V2.4
It is very advantageous, if packets can be matched against one common criterion in one chain, and then passed over for processing against some other common criteria to another chain. For example, packets must be matched against the IP addresses and ports. Then matching against the IP addresses can be done in one chain without specifying the protocol ports. Matching against the protocol ports can be done in a separate chain without specifying the IP addresses.
The Forward Chain is used to process packets passing through the router.
The Output Chain is used to process all packets leaving the router through the interface. Packets originated from the router are processed according to the output chain only.
The firewall rules are applied in the following order:
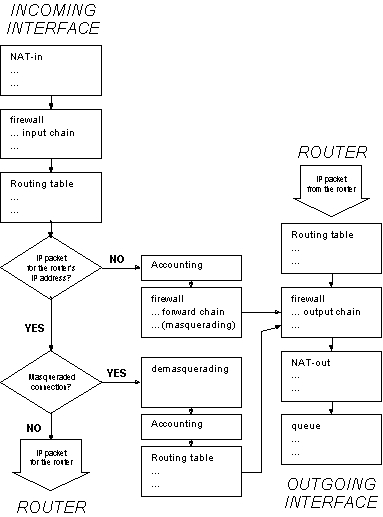
IP packet flow through the router is given in the following diagram:

When processing a chain, rules are taken from the chain in the order they are listed there from the top to the bottom. If it matches the criteria of the rule, then the specified action is performed on the packet, and no more rules are processed in that chain. If the packet has not matched any rule within the chain, then the default policy action of the chain is performed.
The following topics are covered in this manual:
[MikroTik] ip firewall> print # NAME POLICY 0 input accept 1 forward accept 2 output accept [MikroTik] ip firewall>
These three chains cannot be deleted. The available policy actions are:
Note! Be careful about changing the default policy action to these chains! You may lose the connection to the router, if you change the policy to deny or reject, and there are no rules in the chain, that allow connection to the router.
Usually packets should be matched against several criteria. More general filtering rules can be grouped together in a separate chain. To process the rules of additional chains, the 'jump' action should be used to this chain from another chain.
To add a new chain, use the /ip firewall add command:
[MikroTik] ip firewall> add name=router [MikroTik] ip firewall> print # NAME POLICY 0 input accept 1 forward accept 2 output accept 3 router none [MikroTik] ip firewall>
The policy of user added chains is 'none', and it cannot be changed. Chains cannot be removed, if they contain rules (are not empty).
[MikroTik] ip firewall> rule input [MikroTik] ip firewall rule input> print Flags: X - disabled, I - invalid [MikroTik] ip firewall rule input>
There are currently no rules in the input chain. To add a rule, use the add command, for example:
[MikroTik] ip firewall rule input> add ?
Creates new item with specified property values.
action Rule action
copy-from Item number
dst-address Destination address
dst-netmask Destination mask
dst-ports Destination port range
interface Interface name (or all)
log Enable/Disable logging
protocol Protocol
src-address Source address
src-netmask Source mask
src-ports Source port range
target Target chain
tcp-options TCP options
[MikroTik] ip firewall rule input> add dst-ports=8080 protocol=tcp action=reject
[MikroTik] ip firewall rule input> print
Flags: X - disabled, I - invalid
0 protocol=tcp src-address=0.0.0.0/0:0-65535 dst-address=0.0.0.0/0:8080
interface=all action=reject tcp-options=all log=no
[MikroTik] ip firewall rule input>
Argument description:
src-address - Source IP address. Can be in the form address/mask:ports, where mask is number of bits in the subnet, and ports is one port, or range of ports, e.g., x.x.x.x/32:80-81
src-netmask - Source netmask in decimal form x.x.x.x
src-ports - Source port number or range (0-65535). 0 means all ports 1-65535.
dst-address - Destination IP address. Can be in the form address/mask:ports, where mask is number of bits in the subnet, and ports is one port, or range of ports, e.g., x.x.x.x/32:80-81
dst-netmask - Destination netmask in decimal form x.x.x.x
dst-ports - Destination port number or range (0-65535). 0 means all ports 1-65535.
interface - Interface, for which the rule should be used. Can be 'all'.
protocol - Protocol
tcp-options - ( all / sysn / nosyn ). 'nosyn' is for all other options than 'syn'.
action - ( accept / deny / jump / masq / none / reject / return )
target - Name of the target chain, if the action=jump is used
log - Log the action ( yes / no )
If the packet matches the criteria of the rule, then the performed action can be:
Note for V2.3 users, who have upgraded to V2.4:
V2.4 has easier management of firewall rules, since it is possible to select a chain, and all commands do not need to contain the argument value for the chain This difference should be considered, when importing firewall configuration script of V2.3 into the V2.4 router. For example:
[MikroTik V2.4] ip firewall rule input> add protocol tcp src-... [MikroTik V2.4] ip firewall rule input> print [MikroTik V2.3] ip firewall rule> add input protocol tcp src-... [MikroTik V2.3] ip firewall rule> print input
[MikroTik] system logging facility> set Firewall-Log logging=local [MikroTik] system logging facility> print # FACILITY LOGGING PREFIX REMOTE-ADDRESS REMOTE-PORT 0 Firewall-Log local 1 PPP-Account none 2 PPP-Info none 3 PPP-Error none 4 System-Info local 5 System-Error local 6 System-Warning local [MikroTik] system logging facility>
You can send UDP log messages to a remote syslog host by specifying the remote address and port (usually 514). Local logs can be viewed using the /log print command:
[MikroTik] > log print
...
sep/26/2001 17:40:26 user admin logged in at Wed Sep 26 17:40:26 2001
from 10.5.8.203 via telnet
sep/26/2001 17:42:30 Public: input->REJECT, prot TCP(SYN),
10.5.8.48:4366->10.1.1.12:8080, len 60
[MikroTik] > log print
(The format of the log is:
DATE TIME Interface: Chain -> ACTION, protocol,
src-address:port->dst-address:port, packet_length)
Using the Masquerading
Masquerading is a firewall function that can be used to 'hide' private networks
behind one external IP address of the router. For example, masquerading is useful,
if you want to access the ISP's network and the Internet
appearing as all requests coming from one single IP address given to you by the ISP.
The masquerading will change the source IP address and port of the packets
originated from the private network to the external address of the router,
when the packet is routed through it.
Masquerading helps to ensure security since each outgoing or incoming request must go through a translation process that also offers the opportunity to qualify or authenticate the request or match it to a previous request. Masquerading also conserves the number of global IP addresses required and it lets the whole network use a single IP address in its communication with the world.
To use masquerading, a firewall rule with action 'masq' should be added to the forward chain of the router's firewall configuration:
[MikroTik] ip firewall rule forward>
add action=masq interface=Public src-address=192.168.0.0/24
[MikroTik] ip firewall rule forward>
Flags: X - disabled, I - invalid
0 protocol=all src-address=192.168.0.0/24:0-65535
dst-address=0.0.0.0/0:0-65535 interface=Public action=masq
tcp-options=all log=no
[MikroTik] ip firewall rule forward>
If the packet matches the 'masquerading' rule, then the router opens a connection to the destination, and sends out a modified packet with its address as the source and source port above 60000. The router keeps track about masqueraded connections and performs the 'demasquerading' of packets, which arrive for the opened connections.
The list of currently opened masqueraded connections can be viewed using the /ip firewall masqueraded-connections print command:
[MikroTik] > ip firewall masqueraded-connections print detail
0 protocol=tcp src-address=10.5.6.202:3454 dst-address=193.178.150.165:1774
masq-port=61068 expires=00:07:54
1 protocol=udp src-address=10.5.8.203:137 dst-address=63.95.59.228:137
masq-port=61296 expires=00:04:57
[MikroTik] >
Basic Firewall Building Principles
Assume we have router that connects a customer's network to the Internet.
The basic firewall building principles can be grouped as follows:
This can be done by putting rules in the input chain to match packets with the destination address of the router entering the router through all interfaces.
This can be done by putting rules in the output chain to match packets with the destination addresses of customer's network leaving the interface.
This can be done by enabling the masquerading action for rules in the forward chain.
This can be done by putting rules in the forward chain. You can masquerade only those connections, that are allowed, and reject everything else.
Examples of setting up firewalls are discussed later.
Further on, the following examples of using firewall rules are given:
Assume we want to create a firewall, that
The basic network setup is in the following diagram:
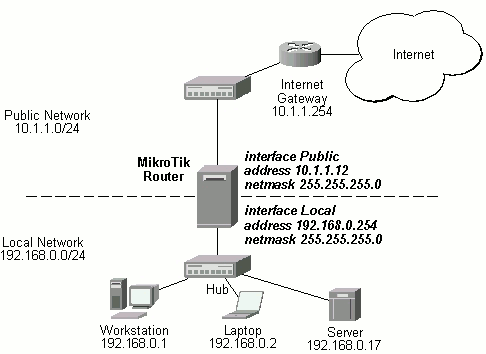
The IP addresses and routes of the MikroTik router are as follows:
[MikroTik] > /ip address print Flags: X - disabled, I - invalid, D - dynamic # ADDRESS NETWORK BROADCAST INTERFACE 0 192.168.0.254/24 192.168.0.0 192.168.0.255 Local 1 10.1.1.12/24 10.1.1.0 10.1.1.255 Public [MikroTik] > /ip route print Flags: X - disabled, I - invalid, D - dynamic, R - rejected # TYPE DST-ADDRESS NEXTHOP-S... GATEWAY DISTANCE INTERFACE 0 static 0.0.0.0/0 A 10.1.1.254 1 Public 1 D connect 192.168.0.0/24 A 0.0.0.0 0 Local 2 D connect 10.1.1.0/24 A 0.0.0.0 0 Public [MikroTik] >
[MikroTik] > ip firewall add name router
[MikroTik] > ip firewall rule router
[MikroTik] ip firewall rule router>
add protocol tcp tcp-option nosyn
add protocol udp
add protocol icmp
add src-addr 10.1.1.16/29
add action reject log yes
[MikroTik] ip firewall rule router> print
Flags: X - disabled, I - invalid
0 protocol=tcp src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=all action=accept
tcp-options=nosyn log=no
1 protocol=udp src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=all action=accept tcp-options=all
log=no
2 protocol=icmp src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=all action=accept tcp-options=all
log=no
3 protocol=all src-address=10.1.1.16/29:0-65535
dst-address=0.0.0.0/0:0-65535 interface=all action=accept tcp-options=all
log=no
4 protocol=all src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=all action=reject tcp-options=all
log=yes
[MikroTik] ip firewall rule router>
Here, we created a new chain 'router' and added rules to it, that
[MikroTik] ip firewall rule input>
add dst-address=10.1.1.12/32 action=jump target=router
add dst-address=192.168.0.254/32 action=jump target=router
[MikroTik] ip firewall rule input> print
Flags: X - disabled, I - invalid
0 protocol=all src-address=0.0.0.0/0:0-65535
dst-address=10.1.1.12/32:0-65535 interface=all action=jump target=router
tcp-options=all log=no
1 protocol=all src-address=0.0.0.0/0:0-65535
dst-address=192.168.0.254/32:0-65535 interface=all action=jump
target=router tcp-options=all log=no
[MikroTik] ip firewall rule input>
Thus, the input chain will match packets with the destination address of the router, and the router chain will accept the allowed connections and reject and log everything else.
To protect the customer's network, we should match all packets with destination address 192.168.0.0/24, that leave the Local interface, and process them against rules of another chain, say, 'customer'. We create the new chain and add rules to it:
[MikroTik] ip firewall> add name=customer
[MikroTik] ip firewall> print
# NAME POLICY
0 input accept
1 forward accept
2 output accept
3 router none
4 customer none
[MikroTik] ip firewall> rule customer
[MikroTik] ip firewall rule customer>
add protocol tcp tcp-option nosyn
add protocol udp
add protocol icmp
add protocol tcp tcp-option syn dst-address 192.168.0.17/32:80
add protocol tcp tcp-option syn dst-address 192.168.0.17/32:25
add protocol tcp tcp-option syn src-port 20 dst-port 1024-65535
add action reject log yes
[MikroTik] ip firewall rule customer> print
Flags: X - disabled, I - invalid
0 protocol=tcp src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=all action=accept
tcp-options=nosyn log=no
1 protocol=udp src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=all action=accept tcp-options=all
log=no
2 protocol=icmp src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=all action=accept tcp-options=all
log=no
3 protocol=tcp src-address=0.0.0.0/0:0-65535
dst-address=192.168.0.17/32:80 interface=all action=accept
tcp-options=syn log=no
4 protocol=tcp src-address=0.0.0.0/0:0-65535
dst-address=192.168.0.17/32:25 interface=all action=accept
tcp-options=syn log=no
5 protocol=tcp src-address=0.0.0.0/0:20 dst-address=0.0.0.0/0:1024-65535
interface=all action=accept tcp-options=syn log=no
6 protocol=all src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=all action=reject tcp-options=all
log=yes
[MikroTik] ip firewall rule customer>
Here, we created a new chain 'customer' and added rules to it, that
[MikroTik] ip firewall rule output>
add dst-address=192.168.0.0/24 interface=Local action=jump target=customer
[MikroTik] ip firewall rule output> print
Flags: X - disabled, I - invalid
0 protocol=all src-address=0.0.0.0/0:0-65535
dst-address=192.168.0.0/24:0-65535 interface=Local action=jump
target=customer tcp-options=all log=no
[MikroTik] ip firewall rule output>
[MikroTik] ip firewall rule forward>
add protocol icmp interface Public
add src-address 192.168.0.17/32 interface Public
add action reject interface Public log yes
[MikroTik] ip firewall rule forward> print
Flags: X - disabled, I - invalid
0 protocol=icmp src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=Public action=accept
tcp-options=all log=no
1 protocol=all src-address=192.168.0.17/32:0-65535
dst-address=0.0.0.0/0:0-65535 interface=Public action=accept
tcp-options=all log=no
2 protocol=all src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=Public action=reject
tcp-options=all log=yes
[MikroTik] ip firewall rule forward>
Here, we added rules to the forward chain, that
[mikrotik] ip firewall rule forward>
add src-address 192.168.0.0/24 action masq interface Public
[MikroTik] ip firewall rule forward> print
Flags: X - disabled, I - invalid
0 protocol=all src-address=192.168.0.0/24:0-65535
dst-address=0.0.0.0/0:0-65535 interface=Public action=masq
tcp-options=all log=no
[MikroTik] ip firewall rule forward>
All outgoing connections from the network 192.168.0.0/24 will have
source address 10.1.1.12 of the router and source port above 60000.
No access from the Internet will be possible to the Local addresses.
If you want to allow connections to the server on the local network,
you should use Static Network Address Translation (NAT).
Please consult the Static NAT Manual for information on how to use NAT.